extundelete is a powerful Linux utility designed to recover deleted files from ext3 and ext4 filesystems. It works by scanning the filesystem for traces of […]
Author: Tech Bytes With Suyash
Unlocking the Secrets of Your Linux System: How Auditd Keeps You One Step Ahead of Threats
Let’s talk about auditd, a powerful tool for monitoring and auditing your Linux system. Have you ever wondered how you can track exactly what happens […]
History Facts of Computer #1
😱 You must know this 👉 The First Computer Bug: The term “bug” originated in 1947 when a moth got stuck in the Harvard Mark […]
Certified Ethical Hacker (CEH V13) Practice Exam Guide
500 Practice Questions and Explanations for Exam Success:Looking to pass the Certified Ethical Hacker (CEH V13) exam and elevate your career in cybersecurity? The CEH […]
Smart Hack: Control The Command Execution Timeline In Linux
The timeout command in Linux allows you to run a command with a time limit. If the command takes longer than the specified time, timeout will automatically […]
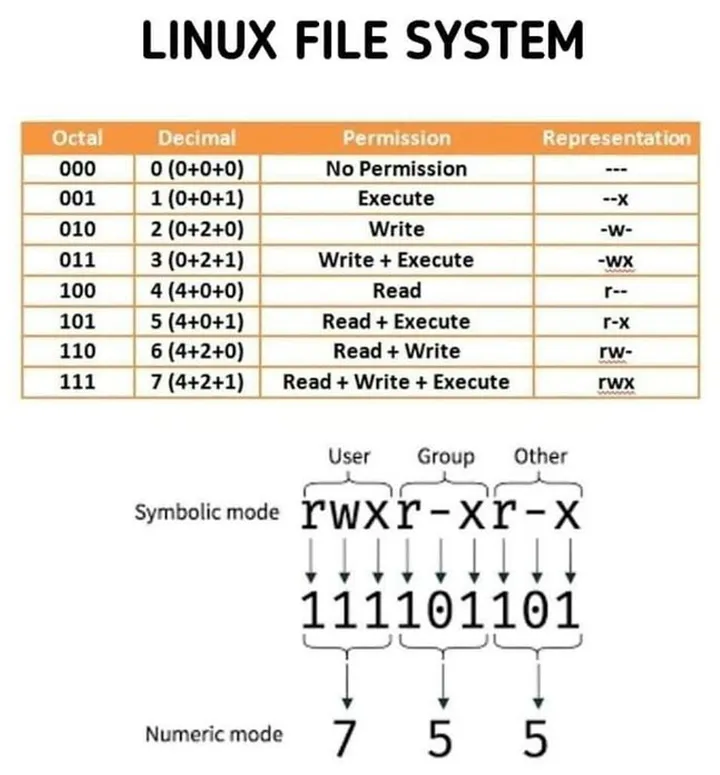
Simplified Linux File Permissions Concept
In Linux, file permissions determine who can read, write, or execute a file or directory. Each file or directory has an associated set of permissions […]
5 Essential Linux Skills Every System Administrator Must Master
For system administrators, Linux skills are essential in managing modern, secure, and efficient IT environments. Linux powers a vast array of servers, databases, and applications, […]
Hidden Secrets Of AWS Aurora And RDS Database Services
Many times, I have to figure out which AWS database service to use and which is best for the use case. This is tricky!! but […]